Most companies have the option to unsubscribe in the email, but there
are still many that do not. Once you learn these three small hacks to
your Gmail address, you can give out an altered version of your email
that will still come directly to your inbox, but will allow you to
create filters to organize the email any way you like. This allows you
to create infinite variations of your Gmail email address.
The Dot Hack
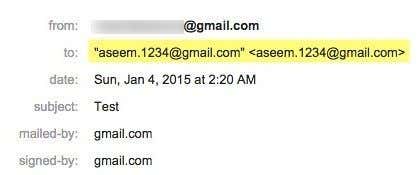
If you didn’t already know, Gmail does not consider any extra dots in
your account name when processing email. So for example, I could write
out my email address as
aseem.1234@gmail.com instead of the normal
aseem1234@gmail.com.
You can add as many dots as you like in any location and the email
will still come to you. This trick usually works the best when signing
up on forums or anywhere online because most forms will accept periods
as an allowable symbol of a typical email address.
The Plus Hack

This Gmail hack has been around for a LONG time and most people already know about it. Simply place a “
+” after your account name and add a word or words to uniquely identify that email address.
For example, I can change my email address to
aseem1234+financial@gmail.com
when signing up at any bank, credit union, investment site, etc. Now I
can create a filter and have all emails related to my financial
activities automatically moved to an appropriate label.
This is much easier than creating a separate filter for each
financial institution. There are many times when the sending email
address used by a financial institution changes and therefore you have
to update your filter. Since your customized Gmail address will never
change, you never will need to worry about updating the filter.
The plus hack is very useful, but the downside is that online forms
sometimes block it because it’s not considered a normal symbol in email
addresses. In that case, use the Dot hack or the Googlemail hack I’m
about to mention.
The Googlemail Hack

Finally, you can change the last part of your email account to
googlemail.com instead of the normal gmail.com! It’s another nifty way
to not give out your main email address. Obviously, if someone else
already knows these tricks, they can easily figure out your original
email address.
So
aseem1234@googlemail.com is exactly the same as
gmail.com. If you want to keep your account name consistent without all
of the dots or plus signs, then you can just use googlemail.com instead.
You might be wondering why this is necessary if you could just create
a filter on the sender email address and organize email that way? That
method works just fine, but like the financial example I gave above,
what if you wanted to give out your email address to some clients of a
small business you are running from home?
If you don’t have a separate
business email address, you could give out an email like
aseem1234+businessname@gmail.com
to all your clients and then have those emails automatically filtered
to a label created for your business emails. Since you don’t necessarily
know the emails of the senders, creating a filter on the customized
To address works much better.
These hacks have been around for a long time and if you’ve been using
Gmail for many years, it’s probably nothing new. However, if you have
recently switched over from Yahoo, Outlook, etc, it’s an extra feature













 we see all the drives listed here. Let me show my drives in My Computer/This PC Now I have Drives Local Disk (H) and (K) as empty. Let me hide H drive. Step 3 : Type select volume h . Syntax : Select volume drive Letter
we see all the drives listed here. Let me show my drives in My Computer/This PC Now I have Drives Local Disk (H) and (K) as empty. Let me hide H drive. Step 3 : Type select volume h . Syntax : Select volume drive Letter  Step 4 : Now disk is selected and ti hide it type remove letter h. Syntax : remove letter drive_letter
Step 4 : Now disk is selected and ti hide it type remove letter h. Syntax : remove letter drive_letter 

 Syntax : assign letter Drive_letter You will get back the drive. Note: Meanwhile even after hiding you can also get inside the drive using Run. Go to Win + R and type the drive_letter.
Syntax : assign letter Drive_letter You will get back the drive. Note: Meanwhile even after hiding you can also get inside the drive using Run. Go to Win + R and type the drive_letter.  enjoy with ti.
enjoy with ti.





 That’ll take care of a lot of the rubbish from your newsfeed with the
exception of sponsored posts and Facebook ads of course, but it’s a
good start.
That’ll take care of a lot of the rubbish from your newsfeed with the
exception of sponsored posts and Facebook ads of course, but it’s a
good start.